Instead of Offering you a Trojan or Ransomware, They use your Machine, your CPU, your Electricity, and Turn that into Money. – Jarkko Turkulainen
It is said that money and profit acts as a huge incentive for equally good and evil acts. Profiteering and the intention to acquire financial resources have emerged as one of the crucial factors behind Cyber Attacks and Threats.
Moreover, this has only exacerbated in the rising trend of online shopping, internet surfing and online financial transactions.
Cyber criminals have developed new forms of crimes that have become more and more sophisticated and difficult to trace and track. One such attack, which has developed in recent times, is that of Cryptojacking. This form of cybercrime involves using the victim’s computing power to mine cryptocurrencies.
So what is Cryptojacking? What is Cryptojacking malware? How to detect Cryptojacking and what are the strategies to prevent Cryptojacking? Let’s delve into these questions.
In this blog, we shall explore what Cryptojacking is and how it works. We will also look at ways to detect and prevent Cryptojacking attacks by identifying the presence of cryptomining code on a computer or mobile device.
What is Cryptocurrency?
Cryptocurrencies are encrypted digital/electronic money/currencies which exist only in the online-virtual world and is used for facilitating financial transactions for the purchase of goods and services.
They are characterised by potential, anonymity and growth and are essentially created by way of fusing computer program and computer processing power, in what is known as the blockchain technology.
The first cryptocurrency which came into prominence was Bitcoin in 2009. It was created by Satoshi Nakamoto (pseudonym) with the intention of developing a digital cash system for guaranteeing transparency and accuracy of balances, accounts and recording of transactions. Unlike conventional currencies, cryptocurrencies are not backed by specific banks or government.
There is no governmental supervision and it is regulated and decentralised in multiple databases across a network of computer systems which are not owned by a single entity.
What is Cryptomining?
The idea of cryptomining can be understood in different ways. In one sense, it refers to the process of verifying transactions happening on the blockchain. In other words, it is the process of adding transactions to the blockchain ledger whereby the miner updates the blockchain and verify that the information is authentic.
In another sense, cryptomining can be seen as a process wherein specialized computer systems execute calculations which are important for securing, recording and verifying transactions on the blockchain.
It entails the involvement of tremendous computing power, mining hardware as well as electricity. But why would individuals incur such huge costs in order to mine coins? The answer lies in the nature of the process of cryptomining.
It operates as a gamble wherein each computer system within a network competes in order to be at the top in guessing a 64-digit hexadecimal number which is known as the ?hash?.
Once the encryption is solved, the solution checks out, and is certified by the system as legitimate; the miner who solved it is rewarded with certain amount of cryptocurrency.
It is evident that the only requisite for conducting cryptomining is the existence of a computer. However, the computer needs to be extremely powerful, supporting enormous power consumption, in order to be able to race with other devices for solving problems on the blockchain.
What is Cryptojacking?
Cryptojacking is a malicious form of cryptomining. It is a variant of Cyber crime which involves hacking into the victim?s computer system, in order to surreptitiously use it for mining cryptocurrency at the cost of the victim?s resources or stealing cryptocurrency from wallets of other individuals.
As already stated, cryptomining involves huge costs as well as large overheads. Thus, by way of cryptojacking, hackers are able to adopt a short cut wherein they are able to avoid the cost and still utilize someone else?s resources, in order to reap profit.
The type of cryptocurrency which happens to be the prime target of Cryptojackers, is Monero. It is preferred over other types of cryptocurrencies, primarily because it is difficult to trace.
Since Cryptojacking merely involves the secretive usage of the victim?s computer system; in one way it might seem to be a harmless crime.
However, there are definitely reasons for concern. In the first place, the whole activity is non-consensual. When you think of what is Cryptojacking attacks, you should be able to understand that it is carried out without the consent or the knowledge of the victim and serves the vested interest of the criminal who starts creating currency, illicitly.
Moreover, Cryptojacking results in serious issues for the victim, primarily in the form of increased processor usage, higher electricity bills, slower computer response time and overheating devices. Once the computer is hijacked, its functionality is compromised, resulting in siphoning of profits to the wallets of Cyber criminals.
What is Cryptojacking and How it Works?
In the section above, we had looked at what is Cryptojacking in terms of its basic definition. In this section, we shall look at what is Cryptojacking in terms of the way/process in which it is conducted.
Cryptojacking is essentially carried out through the installation of the Cryptojacking software by the Cyber criminal into the victim?s system. This is the answer to the question of what is Cryptojacking malware.
The malware works in the backdrop, stealing from cryptocurrency wallets or mining for cryptocurrencies. The process of injecting the malware into the system can be carried out in three ways:
- File-Based Cryptojacking
This involves the unintentional downloading of malware into the system which then runs an executable file, which in turn helps in spreading the cryptomining script throughout the network infrastructure. One of the most common ways in which this process is conducted is through dispatching malicious emails, containing links or attachment which when clicked, helps in downloading the threatening malware. This is quite similar to a phishing attack.
- Browser-Based Cryptojacking
Under this process, a programming language is used to create a cryptojacking script which is then embedded into numerous websites. It provides for the automatic execution of the script and the resultant downloading of the code onto the victim?s computer. Criminals can embed a piece of a Javascript code into a web page or even in out of date WordPress plugins or vulnerable ads.
- Cloud Cryptojacking
Under this strategy, hackers try to get their hands on the API keys of organizations which will enable them to access their cloud services. Once they are able to acquire the access, they use it to draw off system resources for cryptomining, resulting in exorbitant account costs.
All the three strategies mentioned above are basically different ways for compromising a system in order to embed the script. Once the script is embedded, the victim often unconsciously executes it by clicking on the malicious link or browsing to a website loaded with infected ads. This results in the execution of the cryptomining script in the backdrop, without the knowledge of the victim. The script makes use of the system resources and power for solving complex mathematical algorithms in order to mine a block. Every time, the hacker is able to add a new block to the chain, they acquire reward in the form of cryptocurrencies which is then anonymously siphoned off to the digital wallets of these cryptojackers.
As you try to understand what is Cryptojacking, you should remember that this malicious form of cyber crime can be conducted via your Android phones too. The attack can occur through a Trojan which happen to be hidden in a downloaded app. You might even be redirected to an infected website which launches a persistent pop-under. A single phone does have limited processing power; however, when a large number of phones are targeted at the same time, it adds up to a substantial amount of power, enough to draw in the attention of a Cryptojacker.
What is Cryptojacking Malware: Ways to Detect the Same
As already pointed out, the nature of the Cryptojacking malware is such that it does not necessarily result in direct damage for the victim?s computer. However, since it results in utilizing the resources of the system without the knowledge of the victim, it might pose certain indirect disadvantages for the user. This can be in the form of:
- Slow computer performance
- Electricity costs
- Missed opportunities
- IT Labor costs
Once you have developed a fair understanding of what is Cryptojacking Attacks, it is important to be equally aware of some of the signs which might give you a hint that you might have had been a victim of a Cryptojacking attack.
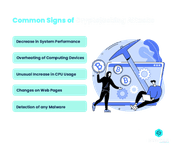
- A noticeable fall in performance of your computing devices
This is one of the first and the most visibly observable signs of a Cryptojacking attack. You should be vigilant and look out for signs of system crash, device running slowly or exhibiting unusually poor performance.
- Overheating of computing devices
Cryptomining in itself, entails the utilization of a considerable amount of resources. Since, Cryptojacking seeks to intrude and make use of other computing devices, it turns out be a highly resource-intensive mechanism. The power consumed and the energy involved in the execution of the process, often results in overheating of batteries in the computing devices. This can result in a permanent damage for the system or at least shorten its lifespan. You should look out for situation wherein the fans of your computing devices may happen to run faster and longer, simply in an attempt to prevent overheating.
- Supervising Websites
Web pages can act as vulnerable points for embedding cryptomining codes. As an individual, you should regularly monitor and observe your own websites for any kind of change to the web pages or any files in the web server.
- Keeping an eye on your CPU usage
Monitoring your Central Processing Unit (CPU) usage is considered to be one of the important strategies for looking out for signs of a Cryptojacking attack. This is because, an unusual increase in CPU usage while you are on a website with little or no media content, can be indicative of cryptomining happening in the backdrop. You can make use of the Task Manager or the Activity Monitor on your computer, for tracking CPU usage.
What is Cryptojacking Attacks: How to Defend yourself?
Prevention and defence strategies against Cryptojacking are not out rightly straight cut measures. This is primarily because it is not always easy to manually detect the intrusion of a Cryptojacking malware, even after the attack has occurred. Similarly, it might be difficult to trace the cause of high CPU usage. Moreover, you might even find it difficult to troubleshoot your system when it is running at its full capacity and extremely slow. So what can you do as an individual to safeguard yourself from such a threat? Let us find out.
- Install a robust Cyber Security program
This is an important defense mechanism as security programs do help in detection of threats across board and can provide for protection against Cryptojacking malware too. It is always wise to ensure regular software updates for your operating systems.
- Using Browser Extensions for blocking Cryptojacking attempts
These are also known as Anti-Cryptojacking extensions. There are a number of extensions which can be installed in some of the popular browsers and help in blocking Cryptojackers and Cryptominers. These include No Coin, minerBlock, Anti Miner and so on.
- Using Ad Blockers
Online ads serve as vulnerable mediums for delivering Cryptojacking scripts to your system. Using ad blockers can help in identifying and blocking Cryptojacking codes.
- Disabling JavaScript
One of the significant measures for preventing Cryptojacking is through disabling JavaScript. This helps in preventing Cryptojacking code from infecting your system.
- Blocking known blacklist sites
This is definitely not a full proof measure as your network and device still remain vulnerable to new Cryptojacking pages. However, it is definitely a somewhat defensive mechanism as you seek to ensure that the sites you visit is a safe one and not one among those known for Cryptojacking.
Conclusion
By now, you must have developed a fair idea of what is Cryptojacking. There is considerable debate on the issue of whether Cryptojacking is on the rise or on a decline. It is important to remember that the frequency and significance of this variant of Cyber attack is directly proportional to the value of cryptocurrencies. Having said that; certain efforts like stringent law enforcement as well as the shutting down of Coinhive (one of the leading sites which dealt with Cryptominers) have had a diminishing effect on Cryptojacking. Even then, it is important to be aware of what is Cryptojacking and how it works. This will help you, not only in being vigilant, but also in undertaking necessary precautionary measures.
Want to know more about other forms of malicious Cyber Attacks like Vishing and ARP Spoofing? Read our blogs on ?What is Vishing?: Everything you Need to know about this Voice Scam? or ?What is ARP Spoofing and How to Prevent ARP Spoofing Attack??
Given the rise of newer and more and more sophisticated Cyber Attacks and crimes on a regular basis; it has not only become indispensable to be aware of the Cyber Security best practices, but in fact the field has come to boast of lucrative career opportunities. Thus, the possibilities are endless and if you wish to make use of this attractive chance, you can be a part of our Cyber Security course. Syntax Technologies, guarantees you end-to-end assistance as you strive to evolve as a Cyber Security expert.