If you Don’t understand Viruses, Phishing and similar Threats, you become more Susceptible to them. If you Don’t know how Social Networks Leak Information that you thought was Private, you’re likely to Reveal much more than you Realize – Brian Kernighan
The expansion of the cyber realm brought in its own share of pros and cons. While it helped individuals connect to the world outside; at the same time, it did somewhere shattered the idea of what was considered to be ?private?.
The virtual world became a dangerous avenue for different forms of cyber attacks and crimes which eventually resulted in revelation of sensitive personal information, identity theft, cyber bullying and so on.
Two such cyber attacks which directly compromises the idea of the private and the personal, shall be discussed here.
This pertains to the topic of Spoofing vs. Phishing. The apparent similarities between the two have made people overlook the difference between Spoofing and Phishing.
However, the issue of Phishing vs. Spoofing is very much a real one and it is important to understand each of them, in its entirety, in order to be able to effectively detect and mitigate each of them.
In this blog, we shall undertake a comparative study on the topic of Spoofing Attack vs. Phishing.
We shall seek to understand the difference between Phishing and Spoofing by highlighting the key points of each. Consequently, we shall take up a tripartite comparison on the issue of Spam vs. Phishing vs. Spoofing.
What is the difference between Phishing and Spoofing?
What is Phishing?
This Cyber Security threat technique is one of the most common forms of cyber attack wherein the intention is to acquire critical data in the form of passwords, credentials, credit card numbers and so on, by sending email, messages and links, disguised from sources which the victims have reason to trust.
The attacker puts up a fake appearance as a trusted entity (legitimate company/person) in order to extract sensitive information from random individuals by manipulating them. Phishing is made successful through different forms of user interaction.
This can be through instant messages or calls for acquiring confidential data such as credit card information, emails containing malicious links resulting in download of risky attachments and so on.
?Examples of Phishing
In this section, we shall look at some of the most common ways in which phishing attacks are carried out.
- Requests for verification of personal data through malicious emails
- Emails or calls from recognized financial institutions like banks, asking for passwords, OTP or PIN
- Emails using the bait of tax refunds to dupe victims
- The use of the phrase ?Click Here? is quite common in such suspicious communication
- Phishing can take place when the DNS of an individual?s router is changed without their knowledge
- You must be used to making payments online, however, you might receive false emails claiming that a particular payment made by you has failed and hence instigate you to take a particular action
- There might be instances wherein you might be redirected to a fraudulent site upon entering the URL in the browser
Types of Phishing
Let us check out some of the most common types of phishing attack.
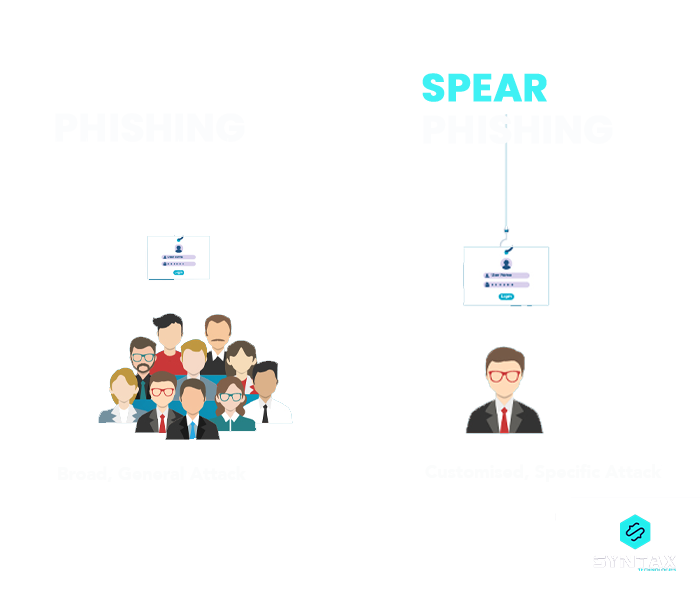
Email Phishing: The phishing attack is carried out through malicious emails. It is the most common form of phishing attack.
Spear Phishing: It is a form of phishing attack wherein the email is sent to specific targets such as specific individuals, business or organizations. Intention might be to steal information or install malware on the targeted victim?s system.
Whaling: Also known as CEO Phishing, this attack is essentially targeted towards business leaders or senior executives of organizations.
Since, it is a highly targeted form of attack and also uses email as the primary medium for carrying out phishing; it is a combination of spear and email phishing. In most cases, the intention is to initiate the transfer of funds.
Clone Phishing: As the name suggests, this attack involves the act of cloning or creating a replica. The attacker clones/creates a replica of a legitimate or genuine email which an individual might have had received from an authentic source.
The forged email is identical to the genuine email and is sent from a spoofed email id. It does contain malicious content like a link which if clicked, results in the installation of malware in the victim?s system.
Angler Phishing: This kind of phishing attack uses social media as the medium for instigating a cyber attack. Attempt is to steal data and information posted on social media platforms and consequently force victims in divulging personal information.
Smishing: This attack makes use of text messages for tricking users. The messages usually involve phone numbers for the user to call or a link to a website which is controlled by the attacker.
Vishing: A Vishing Attack is considered to be a combination of Voice and a Phishing Attack. Vishing can be understood as a voice based phishing attack, meant to extract personal or financial information from the victims over a fraudulent phone call.

Want to know about Vishing in full?, refer to our blog on ?What is Vishing?: Everything you Need to Know about this Voice Scam?
Prevention Strategies
- In case of received emails, double check the source of the same
- Be cautious while opening or downloading attachments. Do open them only when you are convinced that they are from trusted sources
- Completely get rid of emails which involve misspellings within the body of the message or otherwise have an unprofessional tone to it. Also be vigilant of emails which contain sensational subject lines like ?Act Now?, ?Hurry? and so on.
- When you are doubtful of a particular piece of communication, do verify it directly from the sender.
What is the difference between Spoofing and Phishing?
What is Spoofing?
Spoofing ensues when the attacker steals the details of a legitimate user and acquires the identity of a real-time user in order to contact the victim. The primary objective in this kind of attack is to acquire sensitive personal information of the victim.
Herein, an untrustworthy and unknown communication is falsely presented as a legitimate one. Moreover, since the attacker behaves as someone else who exists in the real world, it is another form of identity theft.
Wondering what is ARP Spoofing?, read our blog on ?What is ARP Spoofing and How to Prevent ARP Spoofing Attack??
Examples of Spoofing
- You might be requested to login into a malicious website which might otherwise look like an authentic website of a bank. The objective might be to dupe you in revealing your account information.
- Modification of IP address of the site which might result in hacking of the complete website.
Types of Spoofing
Email Spoofing: Under this type of attack, the attacker seeks to steal and forge the ?from address? in order to make it appear to be from a legitimate source.
Caller ID Spoofing: As the name suggests, here the attack involves a phone number. The number is spoofed in order to look like a local phone number or one which is from a trusted source. Consequently, the victim is coerced in revealing personal information.
DNS Server Spoofing: Here the attacker happens to manipulate traffic. They seek to redirect traffic to different IP addresses so that individuals land up at websites which help to spread malware.
Website Spoofing: In this case the attacker might set up fake websites which might look like a legitimate one. Or else, they might also take over an existing website and change its address. These malicious websites might be malware laced or might instigate you to divulge sensitive data.
IP Spoofing: It involves attempts made at hiding IP addresses of computers. Objective here is to forge the true identity of the sender or impersonate another computer system. It is quite common in case of DDoS Attacks wherein one seeks to hide the source of malicious traffic.
Prevention Strategies
One of the most effective prevention strategies for detecting spoofing attacks, as recommended by most people is to pay attention to and be vigilant of the details within a piece of communication. In doing so, you should look out for:
- Grammatical errors within the communication
- Spelling errors in web pages, emails or URLs
- The nature of sentence structure or instances of odd sentence phrasing
Difference between Spoofing and Phishing
- One of the primary difference between Phishing and Spoofing is in terms of the purpose or goal of the two attacks. While the main objective of phishing is often to extract personal sensitive information and misuse the same; the main objective of spoofing is to wrongfully acquire someone else?s identity. Thus spoofing is also a form of identity theft.
- Spoofing is often considered to be a subcategory or subset of phishing. This is because attackers often assume the pretense of being a legitimate user, before they commit a phishing attack. However, phishing might not necessarily involve spoofing.
- Phishing is carried out using social engineering techniques; while spoofing essentially involves the installation of malicious software and other forms of malware in the system of the victim.
- Since spoofing does not necessarily entail the stealing of personal information, it is not out rightly considered to be a fraud. On the other hand, since phishing entails data theft and leakage of sensitive information, it is considered to be an online fraud.
- Phishing can be of various types such as email phishing, vishing, clone phishing, spear phishing, smishing, whaling and angler phishing. Types of spoofing include email spoofing, caller ID spoofing, DNS server spoofing, website spoofing and IP spoofing.
Spoofing vs. Phishing: A Tabular Comparison
Spam vs. Phishing vs. Spoofing
The idea of Phishing and Spoofing is often confused with another closely related term, which is ?scam?. Let us look at the issue of Spam vs. Phishing vs. Spoofing.
Conclusion
It is evident that the difference between Phishing and Spoofing is an overlooked domain, given the kind of aesthetic similarities between the two phenomenons.
However, no matter how thin the line of difference might be, the line does exist. The distinction is clearer in case of the objective and the nature of the two attacks. Thus, the issue of Phishing vs. Spoofing is definitely a real one.
It is important to remain vigilant and cautious through regulating the nature of your interaction with the cyber realm.
The proliferation of cyber crimes has crossed all predictions over the decades. The increasing sophistication and frequency of cyber attacks, has rendered it imperative to be aware of the different kinds of baits which cyber criminals might use in order to reach out to its targeted victims.
Given the rising demand of the field of Cyber Security, it would only be wise to develop expertise in line with the demands of the domain.
We, at Syntax Technologies, provide you with exactly such an exciting opportunity, right from the comfort of your home. Enrol now for our Cyber Security course.