?There are only two types of companies: those that have been hacked, and those that will be.? – Robert Mueller (FBI, Director, 2012)
The aforementioned statement is not just an acceptance of an unfortunate reality, but it gives us an idea of what is to come. The need for conducting operations online has increased by leaps and bounds in the contemporary scenario. These activities lack concreteness and are at once, highly vulnerable to cyber threats and dangers. This would very much answer the question of ?What is Cyber Security?.
In this blog, you will learn Cyber Security in all its dimensions and we will cover some of the most important concerns which surround the Cyber Security definition.
What is Cyber Security?
In answering the question of what is Cyber Security, it is important to take note of the dynamic nature of the field. Cyber Security can be seen as a discipline which deals with providing protection and security to servers, computer systems, mobiles, programs, systems and networks; with the objective of defending them against malicious digital attacks (Cyber Security threats and Cyber Security attacks). These attacks are essentially aimed at transforming, destroying or acquiring access to sensitive data; demanding ransom from the owners of data, or seeking to disrupt the normal procedure of business.
Why is Cyber Security important?
The digital revolution and the interconnectedness of systems and devices have only heightened the possibility of Cyber Security attacks. These systems and devices rely on the storage and transmission of data which might be in the form of sensitive information; the loss of which is expected to have tremendous negative repercussions. These might include operational and revenue loss, reputational risks and customer aversion, data breaches, misuse of data, extortion attempts and so on. As individuals, notwithstanding the position wherein one might be situated, it is imperative to learn Cyber Security.
Future predictions portray an even grimmer picture of reality with the International Data Corporation anticipating that the global expenditure on instituting a Cyber Security defence is speculated to touch a staggering $133.7 billion by 2022. Moreover, recent events have only served to underline the importance of Cyber Security. In the first week of May 2021, Colonial Pipeline (one of the top U.S. based fuel pipeline operators), had to close down its entire network, in response to a cyber attack which demanded ransom. The attack has not only exposed the vulnerability of the U.S. energy critical infrastructure security, but has duly provided answers to the question of why Cyber Security is important and what is Cyber Security all about.
The importance of Cyber Security has arisen as an important question of national security. This was evident in a much recent confirmation made by Microsoft, as it reported that the Russian hacking group, Nobelium has unleashed another cyber attack as it has sought to target almost 150 organizations across countries. The tech giant pointed out that 25% of the organizations which have been targeted are those which are involved in international development, human rights and humanitarian work. It is important to note that Nobelium was able to use something as secure as an email marketing account of U.S. Agency for International Development (USAID) in order to send phishing emails for duping people in providing sensitive information. This has called for forensic investigation in the matter; however, the magnanimity of the cyber attack duly provides answer to the question of why is Cyber Security important.
Since ?cybersecurity vulnerabilities have become a systemic issue? (Algirde Pipikaite ? cyber strategy lead at World Economic Forum?s Centre for Cybersecurity); demand for experts in the field has spiralled in an unprecedented manner. To learn Cyber Security, even in its most basic form, is no longer an avoidable choice. We at, Syntax Technologies offer you a golden opportunity to become an expert in the field. Resolve all your queries, right from the point of asking questions as basic as what is Cyber Security to the point of evolving as an expert in the field.
Enroll now for our Cyber Security course to become a Cyber Security expert.
Types of Cyber Security
The Cyber Security definition is an encompassing one and it covers a number of different dimensions.
- Network Security: It seeks to safeguard data which travels across devices in the network in order to make sure that it is not intercepted or changed. The components of network security might include firewalls, anti-virus software, IDS/IPS and virtual private networks (VPN).
- Cyber Security vs. Network Security
It is quite evident from the definition of network security and the answer provided to the question of what is Cyber Security, that network security operates as a subset of Cyber Security as the latter provides protection to data found within servers and devices (securing digital data); while the former provides protection to data flowing across the network (securing transit data). While network security deals with issues of protection from DOS attacks (issuing defence against trojans); Cyber Security is concerned with cyber attacks (instituting defence against cyber frauds and crimes).
- Information Security: It provides protection to digital as well as physical data, safeguarding it against disruption, unauthorized access, destruction, disclosure and so on. Information security can be understood as the foundation stone for data security.
- Information Security vs. Cyber Security
Cyber Security can be seen as a subset of information security wherein the former accords protection to the cyber realm; while the latter protects information, regardless of the realm. As the definition of Cyber Security would suggest, it is concerned with cyber attacks (cyber frauds, cyber crime and cyber terrorism), while information security encompasses all forms of threat (modification, unauthorized access, disruption and others), whether in electronic or print form.
- Application Security: It refers to the process of evolving, testing and adding security features within applications in order to protect it from different kinds of Cyber Security threats and vulnerabilities.
- Operational Security: It refers to a specific dimension of risk management which prevents accessibility to sensitive and critical data, by cyber criminals.
- Disaster Recovery and Business Continuity: The two ideas operate as a dyad wherein business continuity focuses on keeping the enterprise operational in the face of a cyber attack; while disaster recovery would deal with the steps taken by the enterprise to ensure restoration of data access. Resilience and expertise are indispensable and they only serve to highlight the importance of Cyber Security.
- Cloud Security: It refers to the entire gamut of policies, technologies and services which ensures protection for cloud application, infrastructure and data from cyber attacks and threats.
- Mobile Security: This category involves the different portable devices (laptops, smartphones, tablets and others) and the protection which is provided to them from dangers involved in wireless computing. The conflation of the idea of mobile devices with that of a necessity has only propelled the need to learn Cyber Security. For instance, mobile applications have witnessed a massive upsurge in usage, which has only been accelerated in the midst of the Covid pandemic. Cyber criminals have sought to capitalize on the situation as they shifted their attention to third party stores, bypassing the official ones, in order to deliver the malware. As per a report by Symantec, ?third-party app stores host 99% of discovered mobile malware?.
Various Cyber Security Attacks
The answer to what is Cyber Security might seem to be a straightforward one. However; there are numerous Cyber Security attacks. These attacks might result in data theft and its misuse. In this blog, we will discuss some of the most common types of Cyber Security attacks.
- Phishing: This Cyber Security threat technique is one of the most common forms of cyber attack wherein the intention is to acquire critical data in the form of passwords, credentials, credit card numbers and so on, by sending email, messages and links, disguised from sources which the victims have reason to trust. Users are duped into clicking these links which grants access to information to the hackers. Phishing is generally of three kinds: whale phishing (high-profile individuals like CEOs are targeted), spear attack (email targets an organization or individual) and pharming (it directs victims to a fake page which bears semblance with the original).
- SQL Injection: This is one of the oldest types of cyber security attack which stands for Structured Query Language. The hacker might send a query which gains entry into the database of the user?s webpage through the SQL injection. This would result in exposure of all sensitive data by the server.
- Ransomware: It refers to a specific kind of malware which debilitates the ability of the user to access their own files. Access to data is sought to be made available in return of a specific amount demanded as ransom which results in aiding the procurement of the decryption key, allowing one to regain access to their data.
- Man-in-the-middle attack: One of the sneakiest type of Cyber Security attack, MIM occurs when criminals position themselves between the server and client and is able to indulge in malicious activities by clandestinely being a part of a critical conversation.
- Distributed Denial of Service (DOS): This type of Cyber Security attack does not directly result in data theft; however, it might result in a system crash. It occurs when a system or network is overwhelmed by unwanted traffic, resulting in the inability to respond to requests.
- Cross-site Scripting (XSS): Under this type of cyber attack, a cybercriminal might send a suspicious code to an otherwise normal website. If the website allows the code to get attached to its own, it bundles the two scripts before it is sent to the user. When the script executes, the hacker would receive a cookie which might help in collecting critical information.
Given the kind of harm which might accrue from any kind of these attacks, it is imperative for individuals to learn Cyber Security and to know about its possible ramifications.
Types of Cyber Security threats
The kind of Cyber Security threats which pose danger for individuals, groups and organizations, can be categorized into three groups:
- Cyber Attack: This is quintessentially aimed at gathering critical data and sensitive information and is often guided by political motives.
- Cyber Crime: These Cyber Security threats include isolated groups or individuals who happen to target their attack with the end intention of acquiring financial gain.
- Cyber Terrorism: It seeks to disrupt the entire electronic system in order to imbue fear and panic.
Cyber Security Best Practices
The Cyber Security definition is an evolving one, especially in terms of the security solutions and remedies which could offer the best form of protection to the cyber realm. One crucial aspect of the importance of Cyber Security is that of end-user protection. The idea behind the same is providing protection to the end-user (individuals) by way of educating them on the appropriate security measures and best practices which could ensure satisfactory protection against cyber-attacks.
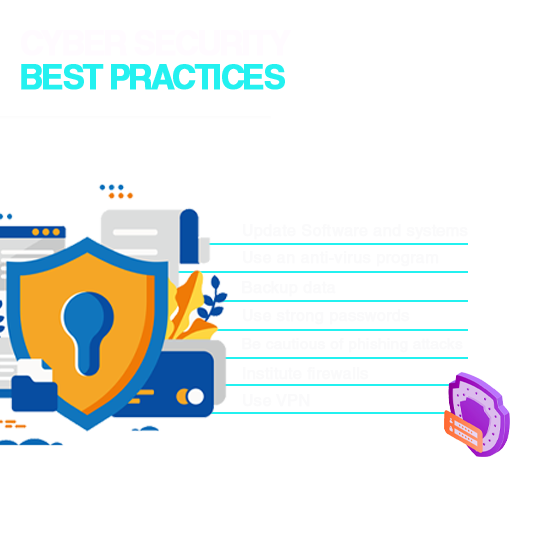
Some of these include:
- Investment in a commendable Cyber Security regime: It is important to ensure that the operating system is up-to-date, and it would be worthwhile to incorporate features which provide protection to vulnerable files and programs.
- It is important to be cautious of one?s own actions in terms of being extra vigilant while downloading software or providing administrative privileges. The latter should only be provided when one is convinced of what exactly it is. This would well answer the question of why it is important to learn Cyber Security.
- As painstaking as it might be, it is important to maintain secured backups of one?s files and data in a regular manner. While there might be several ways of doing this, cloud storage does provide immense benefits in the form of multiple-factor authentication and high level encryption which can be important safeguards against Cyber Security attacks.
While these steps can be taken at an individual level to ensure protection for one?s data and information; the answer to the question of what is Cyber Security goes much beyond that. In response to the demand of the field, initiation into the tools of Cyber Security can be regarded as the first step towards acquiring expertise in the field. Our Cyber Security course at Syntax Technologies provides you with the unique opportunity to acquire training in some of the most important tools in demand, like Bash, QRadar, Palo Alto, Splunk, Redline (FireEye), Nesus, IOC editor (FireEye), Wireshark, Nmap, Burp Suite, Hashcat, Metasploit, Kali Linux and many more.
Career Prospects within the field of Cyber Security
The Cyber Security market represents an important paradox. There is an existing cyber crime epidemic which has propelled the demand for skilled cyber professionals by unprecedented degrees. Organizations are confronted with an acute crisis in the form of workforce shortage; however, the brighter side is that this has accelerated the opportunity for in-demand Cyber Security professionals.
Learning Cyber Security can result in the possibility of earning some of the most lucrative job titles like: Chief Information Security Officer (CISO), Cyber Security Sales Engineer, Cyber Security Architect, Cyber Security Manager/Administrator, Lead Software Security Engineer, Penetration Tester, Information Security Analyst, Bug Bounty Specialist, Cyber Security Lawyer and so on.

As per the data provided by the InfoSec Institute, the median salary of a CISO might be around $140,000+; while CSOonline.com lists it in the range of $140,000-$300,000; while Forbes.com reports the upper end of the salary spectrum of a CISO to be at $420,000.
In case of a Cyber Security Sales Engineer, the annual paid salary is reported to be in the range of $180,000-$220,000; while a Cyber Security Architect might expect an average of $140,820.
Professionals who learn Cyber Security and end up earning the designation of a Cyber Security Manager/Administrator, might earn salaries between $125,00 – $215,000; while the salary of a Lead Software Security Engineer might even exceed that of a CISO and can be as high as $225,000.
The average salary of vulnerability and penetration testers might be at $102,000 and can even touch $130,000; while an Information Security Analyst might fall within the realm wherein the median salary is $95,510.
Conclusion
By the end of this blog, I am sure that even if you have not been able to delve into the intricacies of the domain of Cyber Security in its entirety; you would definitely be convinced of one thing. This pertains to the answer of what is Cyber Security and that it is a phenomenon with unimaginable reach and far reaching impact. We cannot turn back the hands of the clock nor reduce our dependence on connected devices and evolving technology. However, the key lies in taking every possible step in instituting a robust Cyber Security mechanism. Consequently, it has evolved as an extremely lucrative technical field which prepares one to acquire skills which would perhaps, rule the coming times.
We, at Syntax Technologies bring to you the alluring chance to learn Cyber Security from the comfort of your home. Be a part of this enriching online program which would help you to enhance your skills in consonance with the existing requirements of the IT industry.


