One Single Vulnerability is All an Attacker Needs – Window Snyder (Chief Security Officer, Fastly)
The given statement hints at the extent to which we stand vulnerable in the face of Cybersecurity attacks. While technological advancements have ensured commendable benefits for mankind; it has also opened new possibilities for increasing sophistication of cyber threats and attacks. The search for absolute security is in fact considered by many as a vain pursuit with the evolvement of newer forms of threats on a continuous basis.
In the midst of this threatening milieu, we will try to look at the Clickjacking Attack as a significantly potent source of cyber threat.
In this blog, we will try to answer the question of what is Clickjacking, consider Clickjacking: Attacks and Defenses as well as evaluate ways and means for Clickjacking Prevention.
What is Clickjacking?
In this section, we will try to Define Clickjacking, by considering different aspects of a Clickjacking Attack.
Clickjacking or Click Hijacking is also referred to as UI Redress Attack or UI Redressing. A Clickjacking Attack essentially occurs when a user clicks on a webpage element which is disguised as another element within the user interface.
It is an interface based attack wherein a HTML element or an invisible page, embedded in an iframe is displayed over another web page which is actually visible to the user.
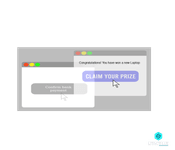
The page which is visible to the user is the decoy website, while the invisible one is the hidden website. In order to understand what is Clickjacking, you can view it as a cyber attack wherein the user unknowingly clicks on some actionable button on the hidden website as he consciously clicks on some entirely different content on the decoy website.
Let us try to understand the Clickjacking Attack through an example. Suppose as a user you happen to visit malicious web pages which showcases an irresistible offer in the form of a holiday deal or a free gift, say you can win a trip to Haiti or stand a chance to win a free laptop. On top of that page; however, the cyber criminal might install an iframe with such directions as ?delete all messages? or links authorizing transfer of money from your bank account or clicks facilitating online purchase of products and so on. This iframe will be invisible to you and will be so placed, that when you as a user happen to click on the button for claiming your free gift, you end up unknowingly clicking on the hidden malicious link which might result in the disclosure of sensitive information, in scams related to money transfer, in malware download and so on. This is how a Clickjacking Script works.
In the event of a Clickjacking Attack, the attacker seeks to target dual entities. The first victim is the host web server which is used as a mere platform for exploiting the Clickjacking Vulnerability; while the second victim is the user who unknowingly ends up clicking on the malicious button and becomes a target to a Clickjacking Attack.
Clickjacking Attack: Its Types
As you try to understand what is Clickjacking, you should be clear of the various kinds and types of Clickjacking Attacks.
- Likejacking
As the name suggests, this kind of attack provides for the manipulation of the Like button on Facebook and other social media platforms as users end up liking pages which they did not actually intend to like in the first place. It is popularly known as Clickjacking Facebook and Twitter too fell victim to this kind of attack which was known as the tweet bomb, in 2009. The attack was launched with tweets which directed users of Twitter to a button which read ?Don?t Click?. In this case, Clickjacking sought to exploit the natural curiosity of humans and as people clicked on the button, they ended up unintentionally posting more messages and tweets which again advertised the same link.
- Cursorjacking
It is a form of UI redressing technique which is responsible for altering the position of a cursor to a different location from where the user perceives it to be. This results in the user believing to take a specific action, while in reality they are undertaking an entirely different action.
- Filejacking
This is a form of a Clickjacking Attack wherein the user unintentionally provides the attacker, access to local files in their system.
- Download of Malware
A Clickjacking Script might include a hijacked link, which when clicked by the user results in the download of malware in the system. This malware can be responsible for destroying the software of the system, in distorting the applications of the program or can become a potential entry point for Advanced Persistent Threats (APTs).
- Scams involving Money Transfer
This is another common type of Clickjacking Attack wherein a user is deceived into clicking on a malicious link on a decoy website whereby he ends up unknowingly authorizing the transfer of money from his own bank account.
- Microphone and Webcam Activation
This kind of Clickjacking Vulnerability is exploited through uploading the Adobe Flash settings of a user over another link. Thus, when the user clicks on the dubious link, they end up unconsciously modifying their Adobe Flash plug-in settings and in fact handing over the access of their microphone and webcam to the attacker.
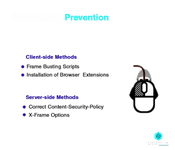
Clickjacking Prevention: Mitigation Strategies
The question of What is Clickjacking cannot be comprehensively answered without considering the different Clickjacking Protection strategies. In order to prevent Clickjacking, it is important to ensure that your webpages are not wrapped in a <IFRAME> or <FRAME> tag. This can be guaranteed through certain precautionary steps from the client as well as the server side.
Client-Side Clickjacking Prevention
1. Frame Busting Scripts
Seeking to prevent Clickjacking through this technique implies that you undertake all efforts in order to ensure that your website does not function within a frame. The strategy is executed with the help of Javascript add-ons which provides instructions to the browser to react in a certain way when a page is loaded in a frame. It generally forces the browser to reload the offset decoy website at the top window, which in turn helps in loading the decoy website on top of the iframe layer. Having said that, it is important to understand that the frame busting technique is not a full proof measure for Clickjacking prevention. Many web browsers block such Javascript code and even those which don?t, can easily be manipulated by attackers to allow the malicious overlay.
2. Installation of Browser Extensions
Browser extensions are considered to be another form of Anti-Clickjacking browser extensions which work through the identification of advanced Clickjacking Attacks. However, a significant disadvantage of such browser extensions, is that, they result in disabling all Javascript on loaded websites. Thus, these extensions impede the functionality of a number of sites which run on Javascipt. Thus, users would be required to specify a whitelist manually, in order to maintain the Javascript experience.
Server-side Clickjacking Prevention
1. Correct Content-Security-Policy
A robust Content Security Policy (CSP), along with its frame-ancestors directive, works as an efficient Cybersecurity strategy against website embedding. An effective CSP policy is capable of being an antidote against iframe embedding and can also provide safeguard against cross-site scripting (XSS). The ?none? option of the frame-ancestors directive is held to be effective towards ensuring that domains do not embed websites in a frame.
2. X-frame Options
This is another strategy used to prevent Clickjacking. The X-Frame Options response header is invoked as a part of the HTTP response of a webpage. It helps in directing whether the browser is allowed to embed the webpages in a frame or not. The X-Frame Options header has three values:
- DENY: The deny directive helps in preventing all attempts to load the website in a frame. This means that it does not allow any domain to display the page in a frame.
- SAMEORIGIN: This directive allows for the framing of your web content, if the parent shares the same origin. Thus, it permits the display of the current page in a frame on another page, but only within the same domain.
- ALLOW-FROM URI: This directive permits only the current or the process page to be shown in a frame, but only in a specific URI.
Conclusion
In this blog, we have looked at What is Clickjacking, its types and kinds as well as different strategies for Clickjacking prevention. Having evolved as a significant form of Cyber Threat, it is imperative for each individual to become aware of the mechanism of a Clickjacking Attack as well as acquaint themselves of the different approaches for preventing the same. The different mitigation strategies do have their own pros and cons and it would be worthwhile to think how best to combine some of them in order to prevent Clickjacking.
We, at Syntax Technologies bring to you the alluring chance to develop your skills as a Cyber Security expert from the comfort of your home. Be a part of this enriching online program which would help you to enhance your competencies in consonance with the existing requirements of the IT industry. Read more about our course here: